- Platform
- Solutions
- Expose and Manage ThreatsContinuously identify, expose and remediate critical threats
- Reduce Attack SurfaceThe roadmap to reducing your attack surface
- Control Subsidiary RiskManage cyber risk across all your subsidiaries
- Cloud SecurityManage your cloud attack surface
- Improve Security PostureReduce risk systematically
- Manage M&A riskEvaluate candidate’s cyber risk
- Learn
- Company
Threat Exposure Radar ExplainedSolutions - Machine learning
Discover all of your domains, subdomains, and IPs. - Connection Intelligence
Map connections in web, DNS, SaaS, and IP. - Global event tracking
Monitor global PKI and domain registration. - Reverse indexing
For domains, IP blocks, and cloud platforms.
Ionix Connective IntelligenceProductAttack Surface Discovery
See your real attack surface The way attackers do
Gain unmatched visibility into all internet-facing assets – and the entire digital supply chain – with IONIX’s patented discovery engine.
Product Highlights
GO FURTHER TO DISCOVER YOUR ATTACK SURFACE
Discover all that matters
IONIX’S Connection Intelligence maps the entire attack surface and its digital supply chain.
Monitor your changing attack surface
Get real-time visibility into your ever-evolving attack surface.
More assets. Less noise
Ensure you’re looking at everything that matters – and nothing that doesn’t.
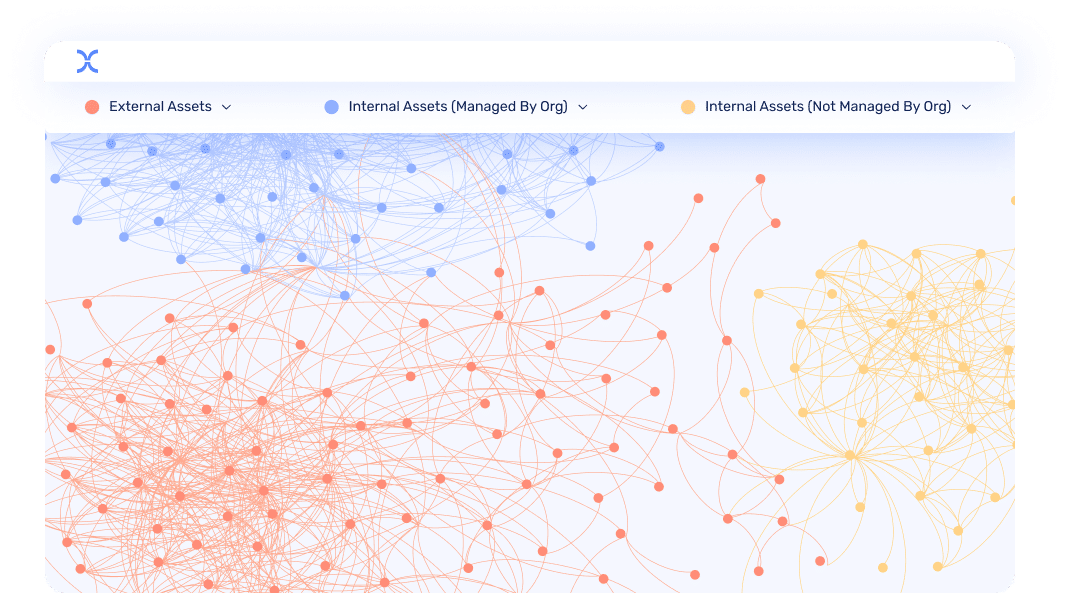
Extended Discovery
Discover all that matters
IONIX’s multi-layered discovery engine creates a comprehensive inventory of your organization from the attacker point of view – including the 20+% of the exploitable attack surface from your digital supply chain:
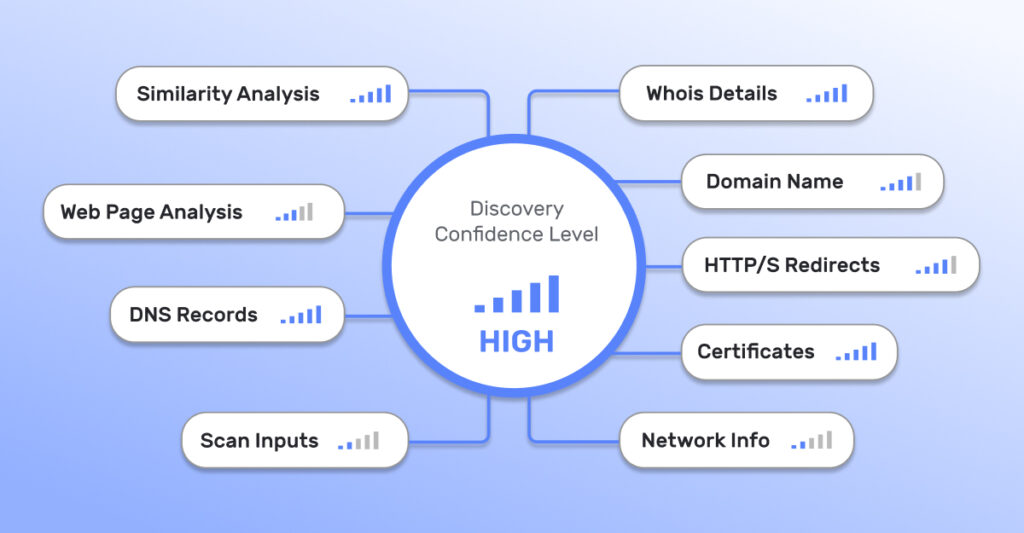
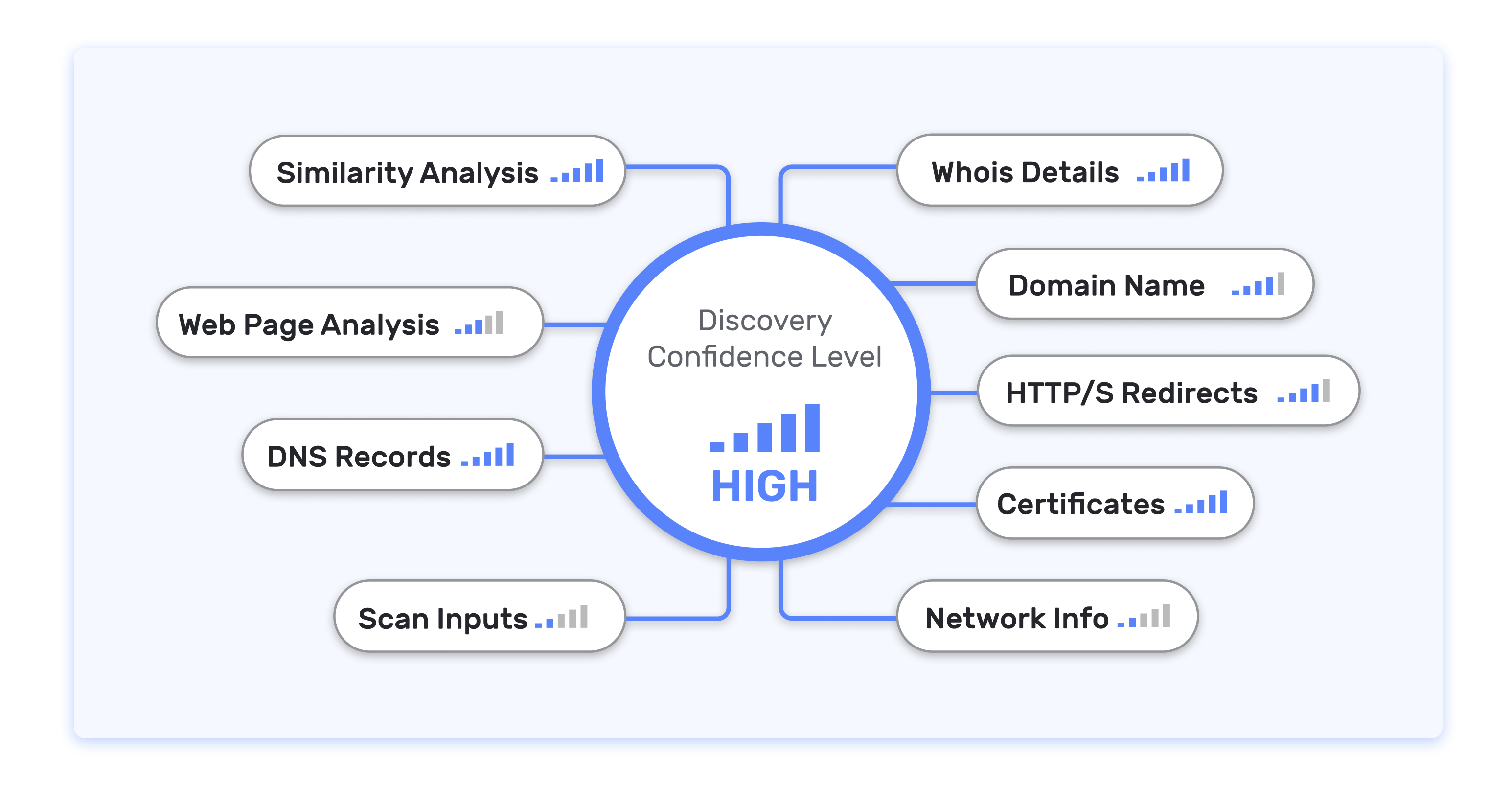
Multi-Factor Attribution
More assets. Less noise.
False positives mean wasted time and money. Using machine learning, IONIX multi-factor asset attribution avoids noisy false positives. By effectively identifying true organizational assets and eliminating irrelevant ones, IONIX provides organizations with a more accurate, efficient, and secure method of managing their attack surface.
Automated Scans
Monitor your changing attack surface
Your attack surface is constantly evolving as infrastructure elements are spun up and decommissioned. IONIX represents your attack surface using a dynamic, graph-based data model – with nodes and dependencies that are continuously updated, and an ever-evolving set of potential kill chains evaluated.
- Solutions