- Platform
- Solutions
- Expose and Manage ThreatsContinuously identify, expose and remediate critical threats
- Reduce Attack SurfaceThe roadmap to reducing your attack surface
- Control Subsidiary RiskManage cyber risk across all your subsidiaries
- Cloud SecurityManage your cloud attack surface
- Improve Security PostureReduce risk systematically
- Manage M&A riskEvaluate candidate’s cyber risk
- Learn
- Company
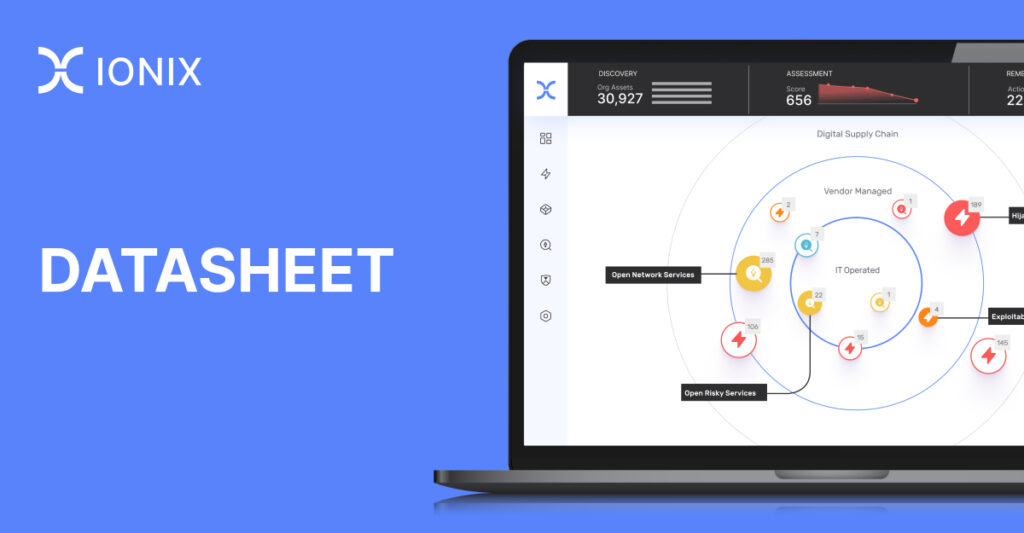
Threat Exposure Radar ExplainedSolutions
Ionix Connective IntelligenceProductProduct highlights
PREVENT ATTACKS BEFORE THEY HAPPEN
Active Protection for always-on security
Automatically neutralize the most immediate exploitable risks to your business.
Seamless integration to your core systems
Directly integrate to core systems for rapid remediation.
Remediation – for the way you actually work
Spend more time fixing (and less time ticket wrangling) with smart workflows.
Automated mitigation
Active Protection for always-on security
With Active Protection, IONIX automatically safeguards the most vulnerable assets from abuse. Dangling DNS records or cloud storage objects (e.g., AWS S3 buckets or Azure blobs) are often vulnerable to attacker hijacking. They can expose web assets to malicious content or DNS takeover. In cases where IONIX detects such vulnerabilities, Active Protection automatically neutralizes the threat – with no action required on your part.
Workflow automation
Seamless integration to your core systems
IONIX integrates with security information and event management (SIEM) systems, SOAR, security operations center (SOC) software, and ticketing systems – to facilitate rapid remediation of critical issues.
Action focused and smart
Remediation – for the way you actually work
IONIX’s smart workflows align remediation tasks with the way that security operations actually work – so you spend less time on routing tickets, and more time resolving critical risks.
- Solutions