- Platform
- Solutions
- Expose and Manage ThreatsContinuously identify, expose and remediate critical threats
- Reduce Attack SurfaceThe roadmap to reducing your attack surface
- Control Subsidiary RiskManage cyber risk across all your subsidiaries
- Cloud SecurityManage your cloud attack surface
- Improve Security PostureReduce risk systematically
- Manage M&A riskEvaluate candidate’s cyber risk
- Learn
- Company
Threat Exposure Radar ExplainedSolutions
Ionix Connective IntelligenceProductCloud security operations
Manage your public
cloud attack surfaceGain visibility into your risk exposure across public cloud platforms. Focus based on deep understanding of exploitability and the potential blast radius. Context to take action and fix what matters most, faster.
Continuous cloud discovery
See your clouds from the attacker’s point of view
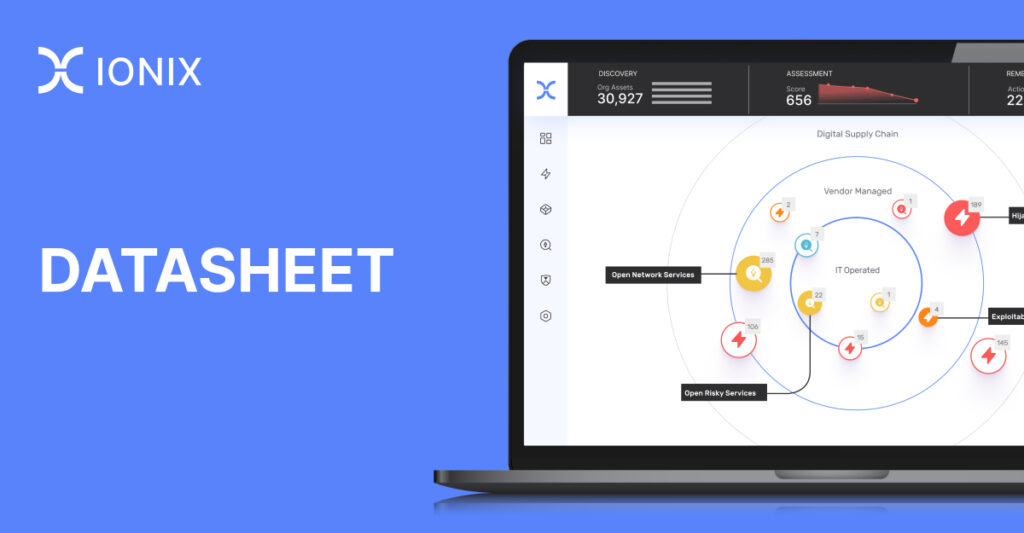
It’s easier than ever for companies to scale and accelerate IT operations by adopting public cloud platforms. This is driving the rise of Shadow IT, where employees create ungoverned cloud assets. As organization’s cloud attack surfaces become more complex and harder to manage, attackers can easily exploit any cloud misconfiguration or exposed vulnerability to breach them.
IONIX combines the attacker’s view and insider’s access of your cloud environments to discover more unknowns, shadow IT, vulnerable assets, and risky connections. Continuously discover your dynamic cloud environments and their digital supply chains.
Digital supply chain security
Identify risky connections in the cloud
Exposed digital supply chain risks pose a threat to your assets and organization. Attackers don’t distinguish between the vulnerable assets you own and the external ones you depend on. With IONIX, you can protect the real attack surface including your internet facing assets and their digital supply chain. Apply Active Protection, automatically, on your riskiest connections to prevent attacks before they happen.
Secure cloud migrations
Migrate securely with adaptive cloud coverage
Cloud migrations are complex projects, often involving multiple vendor partners. As you move across platforms to production, assets are often left exposed or with dangling connections. This is the reason for many breaches on Amazon Web Services, Microsoft Azure, and others.
How can you secure cloud migrations and identify misconfigurations and external risks quickly?
With IONIX, discover exposed cloud assets, shadowIT and connected partner assets. Automatically identify and prioritize misconfigurations and vulnerabilities. Effectively reduce mean time to resolution (MTTR) with clear actions items and integrated workflows.
REQUEST AN ATTACK SURFACE SCAN TODAY
Discover the full extent of your online exposure so you can protect it.
- Solutions