- Platform
- Solutions
- Expose and Manage ThreatsContinuously identify, expose and remediate critical threats
- Reduce Attack SurfaceThe roadmap to reducing your attack surface
- Control Subsidiary RiskManage cyber risk across all your subsidiaries
- Cloud Attack SurfaceClose Security Gaps Across Your Cloud Attack Surface
- Improve Security PostureReduce risk systematically
- Manage M&A riskEvaluate candidate’s cyber risk
- Learn
- Company
Threat Exposure Radar ExplainedSolutions
Ionix Connective IntelligenceProductImprove cyber defense
Optimize your security defenses
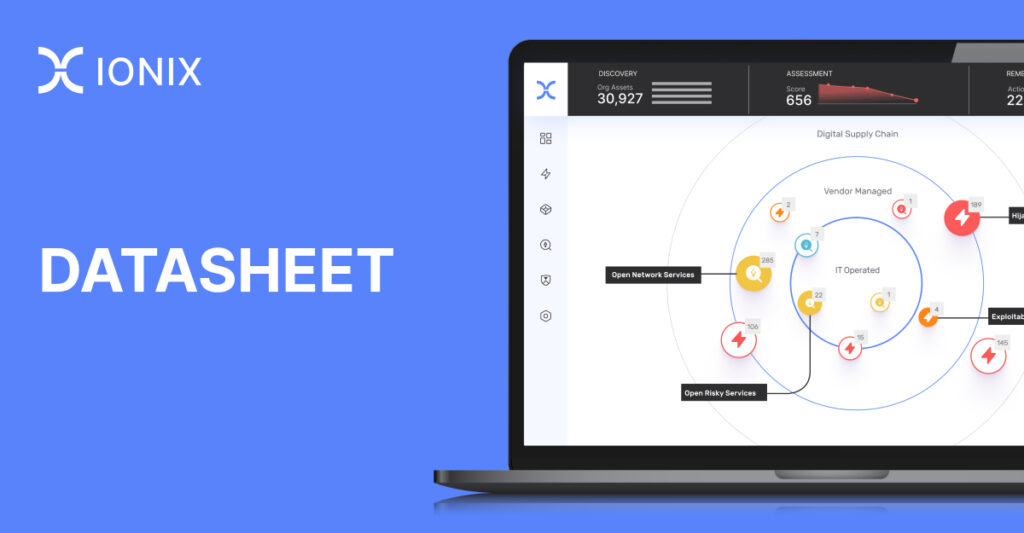
IONIX attack surface management platform helps your security team identify security gaps and accelerate remediation of critical risks, vulnerabilities, misconfigurations, new and evolving threats to improve their cyber security posture. Easy to deploy and operate, the platform provides your security team with the widest coverage of your real attack surface and its digital supply chain – and laser focus on what matters most, further enhancing your security hygiene.
Reduce cyber risk
Focus on critical risks
Today’s security teams are caught between blind spots and alert fatigue. That’s why IONIX is committed to providing the widest coverage and sharpest focus. With IONIX, your security team can identify and quickly remediate exploitable risks across your hybrid IT environments, enhancing your security posture. Using Connective Intelligence, IONIX automatically discovers more, assesses further, applies multi-layered prioritization, and clusters issues into clear action items – while minimizing the noise of false positives and low risk alerts.
Streamline security operations
Remediate more, faster
With IONIX, your security team can focus on actions, not issues – accelerating remediation and reducing noise by clustering multiple issues into a single, clear action item. Action items are automatically attributed to the right subsidiary or functional owner leveraging integrated workflows with SIEM, SOAR and ticketing systems to further streamline your security operations.
REQUEST AN ATTACK SURFACE SCAN TODAY
Discover the full extent of your online exposure so you can protect it.
- Solutions